TryHackMe Write-up: TryHack3M: Bricks Heist
TryHack3M: Bricks Heist is a WordPress exploitation and wallet enumeration room on TryHackMe.

This write‑up reveals how an unauthenticated RCE in a vulnerable WordPress theme led to shell access and uncovered a Bitcoin mining malware tied to an infamous ransomware group.
Click here to go to the answers.Pretext
From Three Million Bricks to Three Million Transactions!
Brick Press Media Co. was working on creating a brand-new web theme that represents a renowned wall using three million byte bricks. Agent Murphy comes with a streak of bad luck. And here we go again: the server is compromised, and they've lost access.
Can you hack back the server and identify what happened there?
Enumeration
I began by adding the machine IP to my /etc/hosts file. Then I got to scanning. My machine IP was 10.10.222.94. Visiting the webpage on port 80 showed a 405 Error. Visiting the webpage on port 443 (HTTPS) showed the following webpage.
NMap
An Nmap scan produced the following results
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
80/tcp open http WebSockify Python/3.8.10
| fingerprint-strings:
| GetRequest:
| HTTP/1.1 405 Method Not Allowed
| Server: WebSockify Python/3.8.10
| Date: Sat, 23 Aug 2025 08:02:04 GMT
| Connection: close
| Content-Type: text/html;charset=utf-8
| Content-Length: 472
| <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01//EN"
| "http://www.w3.org/TR/html4/strict.dtd">
| <html>
| <head>
| <meta http-equiv="Content-Type" content="text/html;charset=utf-8">
| <title>Error response</title>
| </head>
| <body>
| <h1>Error response</h1>
| <p>Error code: 405</p>
| <p>Message: Method Not Allowed.</p>
| <p>Error code explanation: 405 - Specified method is invalid for this resource.</p>
| </body>
| </html>
| HTTPOptions:
| HTTP/1.1 501 Unsupported method ('OPTIONS')
| Server: WebSockify Python/3.8.10
| Date: Sat, 23 Aug 2025 08:02:04 GMT
| Connection: close
| Content-Type: text/html;charset=utf-8
| Content-Length: 500
| <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01//EN"
| "http://www.w3.org/TR/html4/strict.dtd">
| <html>
| <head>
| <meta http-equiv="Content-Type" content="text/html;charset=utf-8">
| <title>Error response</title>
| </head>
| <body>
| <h1>Error response</h1>
| <p>Error code: 501</p>
| <p>Message: Unsupported method ('OPTIONS').</p>
| <p>Error code explanation: HTTPStatus.NOT_IMPLEMENTED - Server does not support this operation.</p>
| </body>
|_ </html>
|_http-server-header: WebSockify Python/3.8.10
|_http-title: Error response
443/tcp open ssl/http Apache httpd
|_http-generator: WordPress 6.5
| http-robots.txt: 1 disallowed entry
|_/wp-admin/
|_http-server-header: Apache
|_http-title: Brick by Brick
| ssl-cert: Subject: organizationName=Internet Widgits Pty Ltd/stateOrProvinceName=Some-State/countryName=US
| Not valid before: 2024-04-02T11:59:14
|_Not valid after: 2025-04-02T11:59:14
| tls-alpn:
| h2
|_ http/1.1
3306/tcp open mysql MySQL (unauthorized)
[SNIP]
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 81.95 seconds
The scan revealed that the site is running WordPress version 6.5. Thus, I ran wpscan against the site.
WPScan
WPScan is a WordPress scanning utility. I ran the scan with the following options:
--url- specifies the targeted URLvp- search for vulnerable pluginsvt- search for vulnerable themesu- show users--disable-tls-checks- disables SSL verification (the scan won't run without this option)--api-token- WPScan will not output vulnerability data without a valid API token. You can register for a free account on their site to obtain a token.--output- specifies the output file
root@ip-10-10-109-175:~# wpscan --url https://bricks.thm --enumerate vp,vt,u --disable-tls-checks --api-token "API TOKEN" --output wpscan.output
[SNIP]
[i] Theme(s) Identified:
[+] bricks
| Location: https://bricks.thm/wp-content/themes/bricks/
| Readme: https://bricks.thm/wp-content/themes/bricks/readme.txt
| Style URL: https://bricks.thm/wp-content/themes/bricks/style.css
| Style Name: Bricks
| Style URI: https://bricksbuilder.io/
| Description: Visual website builder for WordPress....
| Author: Bricks
| Author URI: https://bricksbuilder.io/
|
| Found By: Urls In Homepage (Passive Detection)
| Confirmed By: Urls In 404 Page (Passive Detection)
|
| [!] 5 vulnerabilities identified:
|
| [!] Title: Bricks < 1.9.6.1 - Unauthenticated Remote Code Execution
| Fixed in: 1.9.6.1
| References:
| - https://wpscan.com/vulnerability/8bab5266-7154-4b65-b5bc-07a91b28be42
| - https://twitter.com/calvinalkan/status/1757441538164994099
| - https://snicco.io/vulnerability-disclosure/bricks/unauthenticated-rce-in-bricks-1-9-6
|
| [!] Title: Bricks < 1.9.6.1 - Unauthenticated Remote Code Execution
| Fixed in: 1.9.6.1
| References:
| - https://wpscan.com/vulnerability/afea4f8c-4d45-4cc0-8eb7-6fa6748158bd
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2024-25600
| - https://www.wordfence.com/threat-intel/vulnerabilities/id/b97b1c86-22a4-462b-9140-55139cf02c7a
|
| [!] Title: Bricks < 1.10.2 - Authenticated (Bricks Page Builder Access+) Stored Cross-Site Scripting
| Fixed in: 1.10.2
| References:
| - https://wpscan.com/vulnerability/e241363a-2425-436d-a1b2-8c513047d6ce
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-3410
| - https://www.wordfence.com/threat-intel/vulnerabilities/id/ba5e93a2-8f42-4747-86fa-297ba709be8f
|
| [!] Title: Bricksbuilder < 1.9.7 - Authenticated (Contributor+) Privilege Escalation via create_autosave
| Fixed in: 1.9.7
| References:
| - https://wpscan.com/vulnerability/d4a8b4de-a687-4e55-ab71-2784bef3fc55
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2024-2297
| - https://www.wordfence.com/threat-intel/vulnerabilities/id/cb075e85-75fc-4008-8270-4d1064ace29e
|
| [!] Title: Bricks Builder < 2.0 - Unauthenticated SQL Injection via `p` Parameter
| Fixed in: 1.12.5
| References:
| - https://wpscan.com/vulnerability/c3bed5af-5f31-4993-9d37-dd843a48e57c
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2025-6495
| - https://www.wordfence.com/threat-intel/vulnerabilities/id/5ac49a00-dabc-4cd9-9032-c038ede3fd8f
|
| Version: 1.9.5 (80% confidence)
| Found By: Style (Passive Detection)
| - https://bricks.thm/wp-content/themes/bricks/style.css, Match: 'Version: 1.9.5'
[i] User(s) Identified:
[+] administrator
| Found By: Rss Generator (Passive Detection)
| Confirmed By:
| Wp Json Api (Aggressive Detection)
| - https://bricks.thm/wp-json/wp/v2/users/?per_page=100&page=1
| Rss Generator (Aggressive Detection)
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[+] WPScan DB API OK
| Plan: free
| Requests Done (during the scan): 2
| Requests Remaining: 23
[+] Finished: Tue Aug 26 17:21:30 2025
[+] Requests Done: 595
[+] Cached Requests: 296
[+] Data Sent: 154.735 KB
[+] Data Received: 205.124 KB
[+] Memory used: 259.449 MB
[+] Elapsed time: 00:00:14The scan results were very useful. The site's template, Bricks, is vulnerable to an Unauthenticated Remote Code Injection vulnerability (CVE-2024-25600).
Exploitation
Proof-of-concept (PoC) exploit code for the vulnerability is available on GitHub. I used the PoC found here.
A quick run of the exploit provided me with shell access via the Apache user in the /data/www/default directory. I grabbed the flag from the suspicious text file by running cat *.txt | grep "THM"
The following files were also available. Based on these files, I made the assumption that the site is running PhpMyAdmin. Then I dug into the wp-config file. Configuration files are always worth checking. Bad devs love to leave plaintext credentials lying around.
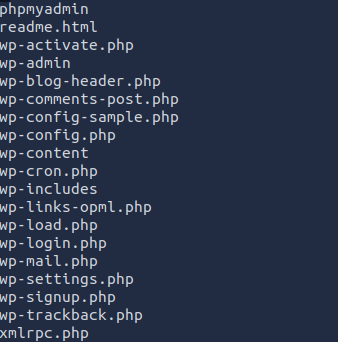
Oh, look credentials for the site's database.
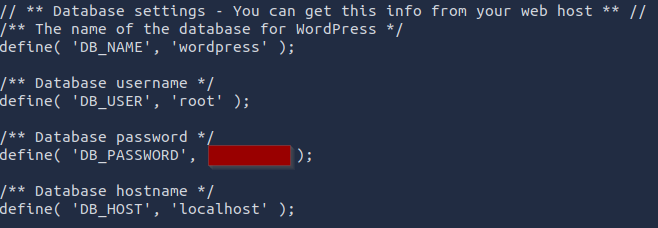
I navigated to https://bricks.thm/phpmyadmin and authenticated with the found credentials. Navigating to the wordpress database provided me with the option to interact with 12 tables.
The wp_users table revealed the site's administrator credentials.
administrator:$P$BYft/ZYThkTPfDb6R2Jzpiu5bkbE8U1
However, these credentials are unnecessary for the investigative questions posed by TryHackMe.
Service Enumeration
I began looking at the running services by using the systemctl --state=running command. This provided the name of the service affiliated with the suspicious process. However, it does not answer the second question.
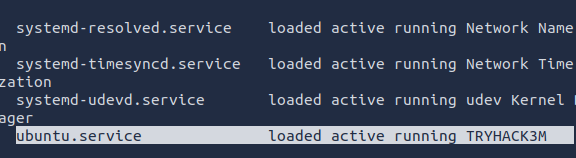
I dug deeper into ubuntu.service to find the name of the suspicious process.
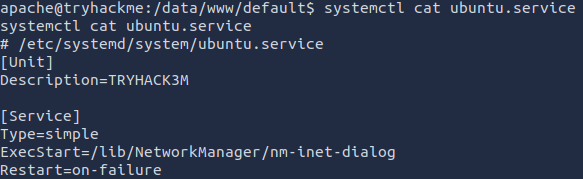
The nm-inet-dialog process is running from the /lib/NetworkManager directory, so I went there to continue the investigation.
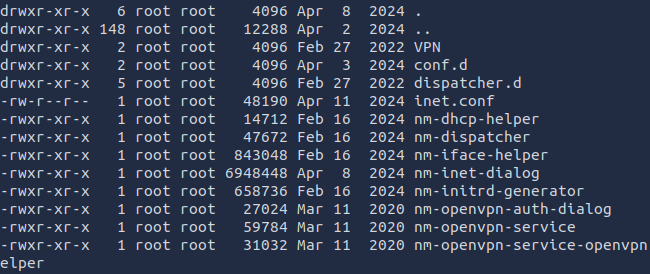
Once there, I analyzed all configuration files for anything useful. The inet.conf file was revealed to be a Bitcoin miner! Don't you love a good log file?
apache@tryhackme:/lib/NetworkManager$ head inet.conf
head inet.conf
ID: 5757314e65474e5962484a4f656d787457544e424e574648555446684d3070735930684b616c70555a7a566b52335276546b686b65575248647a525a57466f77546b64334d6b347a526d685a6255313459316873636b35366247315a4d304531595564476130355864486c6157454a3557544a564e453959556e4a685246497a5932355363303948526a4a6b52464a7a546d706b65466c525054303d
2024-04-08 10:46:04,743 [*] confbak: Ready!
2024-04-08 10:46:04,743 [*] Status: Mining!
2024-04-08 10:46:08,745 [*] Miner()
2024-04-08 10:46:08,745 [*] Bitcoin Miner Thread Started
2024-04-08 10:46:08,745 [*] Status: Mining!
However, it does not immediately reveal the wallet's address. I went to CyberChef to decode the ID (formula here) and was given the following result:
bc1qyk79fcp9hd5kreprce89tkh4wrtl8avt4l67qabc1qyk79fcp9had5kreprce89tkh4wrtl8avt4l67qaUpon closer examination, a repeating string is visible. The first half of the repeating string is the wallet address of the miner instance.
Looking up the wallet on BlockChain gave more information about the wallet's transactions.
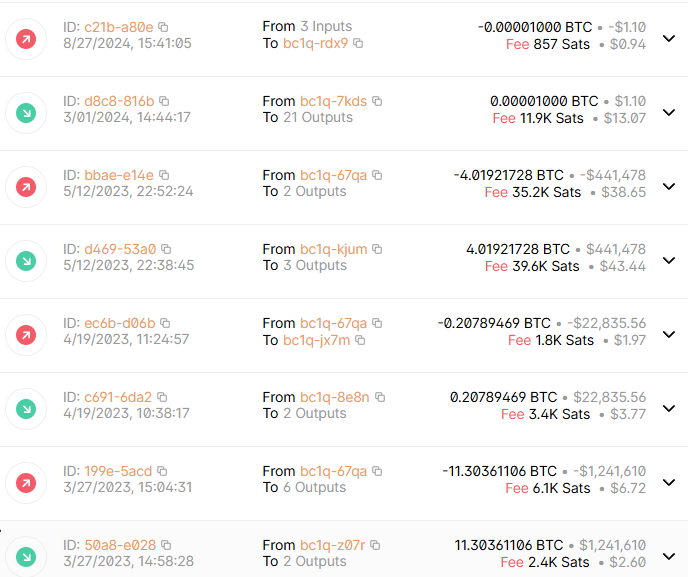
One of the transactions was fruitful: bc1q5jqgm7nvrhaw2rh2vk0dk8e4gg5g373g0vz07r. Googling this transaction immediately led me to https://ofac.treasury.gov/recent-actions/20240220, which revealed the wallet's affiliation with the LockBit ransomware group.
Thank you very much for reading this write-up. If you enjoyed it, please sign up for my newsletter. You'll be notified whenever I write a new post.
Answers
What is the content of the hidden .txt file in the web folder?
THM{fl46_650c844110baced87e1606453b93f22a}
What is the name of the suspicious process?
nm-inet-dialog
What is the service name affiliated with the suspicious process?
ubuntu.service
What is the log file name of the miner instance?
inet.conf
What is the wallet address of the miner instance?
bc1qyk79fcp9hd5kreprce89tkh4wrtl8avt4l67qa
The wallet address used has been involved in transactions between wallets belonging to which threat group?
LockBit




