TryHackMe: Vulnerabilities 101

Task 1: Introduction
Read this task!
No task, click the button
Task 2: Introduction to Vulnerabilities
A vulnerability, per NIST, is a weakness in an information system, system security procedures, internal controls, or implementation that could be exploited or triggered by a threat source.
There are many types of vulnerabilities. The five main categories of vulnerabilities are listed below:
Questions
An attacker has been able to upgrade the permissions of their system account from "user" to "administrator". What type of vulnerability is this?
Operating System
You manage to bypass a login panel using cookies to authenticate. What type of vulnerability is this?
Application Logic
Task 3: Scoring Vulnerabilities (CVSS & VPR)
Vulnerability scoring is the process of determining the potential risk and impact a vulnerability may have on a system. There are two common models: CVSS and VPR.
Common Vulnerability Scoring System (CVSS)
CVSS was first introduced in 2025. Scoring is based on many factors, but three of the most important are:
- How easy is it to exploit the vulnerability?
- Do exploits exist for the vulnerability?
- How does this vulnerability interfere with the CIA triad?
Scoring ranges from 0 - 10 and has ratings from None to Critical. CVSS was not designed to prioritize vulnerabilities, only to assign a value of severity. CVSS is a free framework to adopt and is recommended by NIST.
Vulnerability Priority Rating (VPR)
The VPR framework was developed by Tenable and was created with the goal of scoring vulnerabilities based on their risk to an organization. It includes a None/Informational category, unlike CVSS. However, it is not free to use. Additionally, scores may change over time as risk is reassessed.
Questions
What year was the first iteration of CVSS published?
2005
If you wanted to assess vulnerability based on the risk it poses to an organization, what framework would you use?
VPR
If you wanted to use a framework that was free and open-source, what framework would that be?
CVSS
Task 4: Vulnerability Databases
Key Terms
NVD - National Vulnerability Database
The NVD website lists all publicly categorised vulnerabilities. Vulnerabilities are classified under "Common Vulnerabilities and Exposures" (CVE). CVEs have the formatting of CVE-YEAR-IDNUMBER.
Exploit-DB
Exploit-DB contains exploits for software and applications stored under the name, author, and version of the software or application. Exploit-DB can be used to look for Proof of Concepts (POCs) to verify exploits.
Questions
Using NVD, how many CVEs were published in July 2021?
1554
Who is the author of Exploit-DB?
OffSec
Task 5: An Example of Finding a Vulnerability
When looking for vulnerabilities, pay attention to application version numbers. Use these, alongside the name of the service, to query ExploitDB. Public exposure of version numbers is called Version Disclosure.
Questions
What type of vulnerability did we use to find the name and version of the application in this example?
Version Disclosure
Task 6: Showcase: Exploiting Ackme's Application
Activity
Blurb: It is your first week on the job as Jr. Penetration tester at ThePentestingCo. For your first engagement, you are shadowing a Sr. Penetration Tester within the company.Deploy the site attached to this task and follow the steps that the Sr. Penetration Tester took to exploit a vulnerability against ACKme IT Service's infrastructure.Complete the engagement to retrieve a flag.
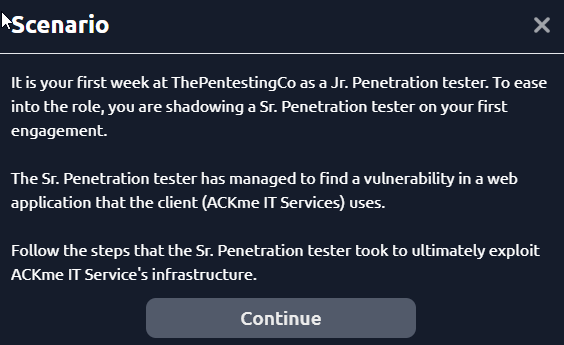
We begin the engagement in an email environment. We are informed to only test a specific IP address.
IP address to test: 240.228.189.136
We then move on to the Information Gathering portion of the exercise.
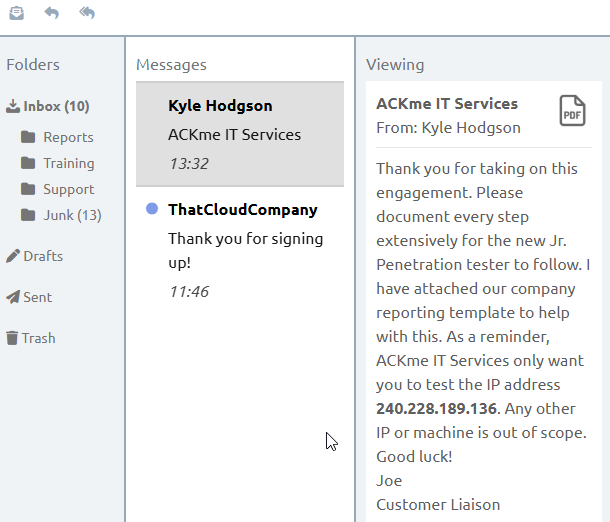
At this stage, the Sr. Penetration Tester has used a public service that compiles some details about the target company.
As we can see, ACKme IT Services provide IT services to 800+ clients. This information is useful because we can begin to think of possible software that they are using for us to attack. For example, helpdesk or a support application.
With this information, we proceed to the enumeration part of the exercise.
The Sr. Penetration tester now moves onto the enumeration and scanning stage of the engagement. This stage helps establish services and applications running on ACKme's infrastructure.
We can use the information gathered from this scan to begin to understand what services may be viable to attack. For example, a webserver hosting a website.
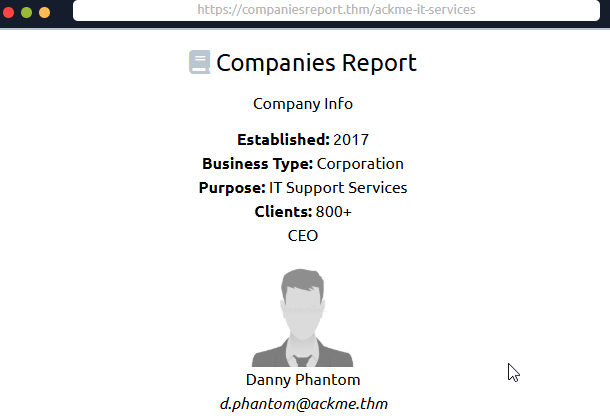
Recall from our Email, we are given one IP address 240.228.189.136. Try scanning this IP address yourself...
At this point, the user is instructed to run a Network Map (nmap) scan of the IP address. Nmap scans provide information about ports and their services.
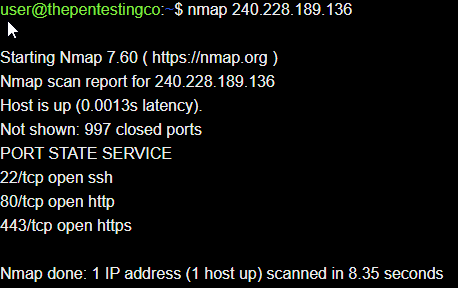
With our information gathered, we begin testing the application for vulnerabilities. A version number is revealed
Using the information gathered from stage two of the penetration engagement. The Jr. Penetration tester has visited the target in their web browser and has been greeted with a login page.
The Sr. Penetration tester guesses some random passwords such as 'admin' and 'admin' to no avail. They notice a version number of the application 1.5.2 and takes a note of this. This will be useful for the next stage.
Continue on to the Vulnerability Research phase of the activity.
The Sr. Penetration tester recalls that ACKme IT Services uses an application called ACKme Portal that has a version number of 1.5.2. The Sr. Penetration Tester visits a vulnerability & exploit database called 'Vulnerability Bank™'.
This website stores details of vulnerabilities and exploits for applications. The Sr. Penetration Tester searches this site for the software that was discovered in stage three. They're in luck! There is one vulnerability listed for that application & version: Remote Code Execution (RCE).
RCE vulnerability allows commands to be executed on the target's system. The Sr. Penetration Tester could use this vulnerability to gain access to the console of the target. Try searching Vulnerability Bank™️ for an exploit for ACKMe Portal 1.5.2 and
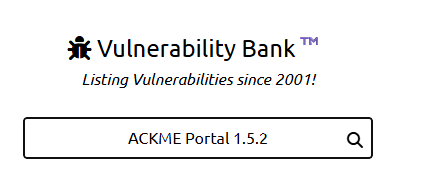
Finally, we move on to the exploitation phase of the exercise.
Accumulating the information from all the previous stages, the Sr. Penetration Tester uses the exploit downloaded from Vulnerability Bank™️ against ACKme's web application on 240.228.189.13.
The exploit is successful and abuses the Remote Code Execution (RCE) vulnerability to launch a reverse shell on ACKme's infrastructure.
From here, the Sr. Penetration tester can look for files of value such as passwords, backups or application source code.
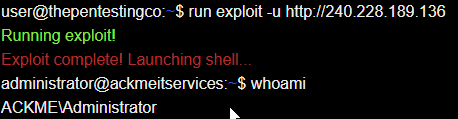
The flag is then revealed.
Question
Follow along with the showcase of exploiting ACKme's application to the end to retrieve a flag. What is this flag?
THM{ACKME_ENGAGEMENT}
Task 7: Conclusion
Press the complete button and move on to your next room!
I hope you enjoyed this walkthrough of the TryHackMe Vulnerabilities 101 room!




