HackTheBox Write-Up: SpookyPass
This is a beginner-friendly Hack The Box reversing write-up showing how to find passwords and extract flags using IDA, strings, and static analysis.

SpookyPass is a reverse engineering challenge on HackTheBox.
I unzipped the challenge files and opened the pass file in IDA.
It became evident that this is a password challenge. If the user provides the correct password, the user will be admitted to the party (aka given the flag).
The basic flow of the program is seen below.
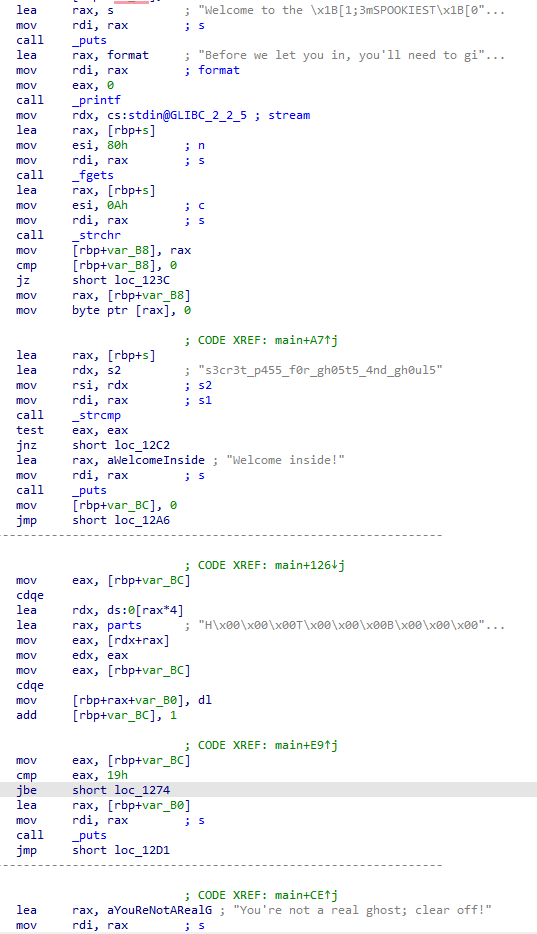
Luckily for us, the secret password is shown in plain text. The secret password is s3cr3t_p455_f0r_gh05t5_4nd_gh0ul5. Finding plaintext passwords in a binary is a common beginner challenge in Capture The Flag (CTF) competitions.
An easy way to find plaintext leaks is to run strings on your file.
Upon entering the secret password, you will see the flag. I chose not to run the binary for this challenge. I found the flag string in the decompiled code and used a regex to extract it.
'H',0,0,0,'T',0,0,0,'B',0,0,0,'{',0,0,0,'u',0,0,0,'n',0,0,0,'0',0,0
0,'b',0,0,0,'f',0,0,0,'u',0,0,0,'5',0,0,0,'c',0,0,0,'4',0,0,0,'t',0
0,0,'3',0,0,0,'d',0,0,0,'_',0,0,0,'5',0,0,0,'t',0,0,0,'r',0,0,0,'1' 0,0,0,'n',0,0,0,'g',0,0,0,'5',0,0,0,'}',0Regular expression: '([^']*)'
Flag: HTB{un0bfu5c4t3d_5tr1ng5}
Thank you for visiting the site! If you enjoyed this post, please consider subscribing to my mailing list. I periodically post write-ups, security analyses, and whatever I find interesting. 😄




